Team OS : Your Only Destination To Custom OS !!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Locked moqs Recovery
- Thread starter qime123
- Start date
- Status
- Not open for further replies.
- Downloaded
- 35.5 GB
- Uploaded
- 3.9 TB
- Ratio
- 111.28
- Seedbonus
- 5,679
- Upload Count
- 265 (265)
Member for 7 years
Dear user, please check your inbox for a possible solution.
Chuck
🤴 Super Admin
- Downloaded
- 300.6 GB
- Uploaded
- 2.9 TB
- Ratio
- 9.93
- Seedbonus
- 593,089
- Upload Count
- 24 (26)
Member for 5 years
Well done for picking up on this. I didn't know what MOQS is.Dear user, please check your inbox for a possible solution.
qime123
Member
- Downloaded
- 358 GB
- Uploaded
- 372.8 GB
- Ratio
- 1.04
- Seedbonus
- 8,180
- Upload Count
- 0 (0)
Member for 8 years
is form a friends laptop some kinds download free stuffAny idea where you got it? What did you install?
Look on YT I see a few guides for removal.
qime123
Member
- Downloaded
- 358 GB
- Uploaded
- 372.8 GB
- Ratio
- 1.04
- Seedbonus
- 8,180
- Upload Count
- 0 (0)
Member for 8 years
I think you can close the thread cant decrypt .. i try everything even
ShadowExplorer
qphotorec_win.exe
Recovery disk
EMSISOFT Decryptor
youtube guide also cant
I found the key but not usable
clean format only option
total virus over 1k found and after recovery, some file is too damaged
ShadowExplorer
qphotorec_win.exe
Recovery disk
EMSISOFT Decryptor
youtube guide also cant
I found the key but not usable
clean format only option
total virus over 1k found and after recovery, some file is too damaged
- Downloaded
- 510.5 GB
- Uploaded
- 24.8 TB
- Ratio
- 49.8
- Seedbonus
- 28,082
- Upload Count
- 1 (1)
Member for 7 years
Ok guys and girls, this starts to look like a chit chat so...
Facts:
Sorry for the bad news but that's reality and I don't like to give people fake hopes. This thread will close soon, just leaving it on for possible questions, and I hope we all learned something.
FYI: For those who may not know, most of the time when we see a 4 letter word like ZZLA, WWKA, GUJD, UFWJ, MOQS, HHQA, PAAS, etc it probably means ransomware.
Facts:
- Ransomware is not something magical. It doesn't get transmitted without your will or without you doing anything. It's a virus-like or malware-like program and as such, it needs to have an entry point in your system. Either by email like "open this attachment to win $10.000.000" or masking as a program, or addon or something similar a user has to execute it in order to get infected.
- Once you get the ransomware and If it detects the internet, it gets a unique key from its server. Once that happens, and for the time being, your files will get encrypted with a unique key that was applied to you ONLY. That key is virtually impossible to be found and only the manufacturer knows it. If it doesn't detect the internet (highly unlikely) then it uses one of the predefined keys which maybe can be found. Assume tho that in your case it got in contact with its command and deployment server.
- You can use a search engine and search for "ransomware decryptor tools" and see which one is offering to try to decrypt your specific variant and give it a try.
- One lesser-known feature of windows is called volume shadow copies which sadly a lot of custom windows disable. This makes a shadow copy (backup) of our file when we modify it and it's better to be thought of as a versioning tool. By using this tool (I include the URL in case there is a new update in the future)
https://www.shadowexplorer.com/downloads.htmlyou can explore possible shadow copies of files (again, if you haven't disabled the service) and maybe you get lucky. (Update) Some of the new forms of ransomware also erase shadow copies but still give it a try. - Some ransomware in order to be able to encrypt as many files as possible without getting caught by showing high system activity, they only encrypt the first 150kb of a file and not the entire file. So in some cases of large video files, (after making a copy) you can rename them and try to open them in a video editor. There is a chance you will get few seconds of static at the start but salvage the video. The same can happen for some RAR/ZIP/7z files as they can repair and only discard the bad portion but still salvage some files.
- Tho the new ransomware disable system restore, give it a try to at least restore some of your programs. Sadly system restore doesn't restore user data.
- Of course all the above need to happen AFTER you clean your system from the malware. The process is the same as any virus and instructions can be found on the net. Even better, remove and disinfect the hard disk using another system when possible.
- If all the above fail, store the files somewhere and hope in the future that a fix will be made/released.
- Honestly, after you try anything you can, format the PC with new windows unless you are THAT good with PCs. I would never trust a PC with malware even if it got removed. All it takes is to forget one file or not Medicines the entry point and you will be having the same problem again soon.
Same as any other malicious program and virus
- Use common sense. If you find somewhere a Medicines or a program that you can't find anywhere else... guess what, Ransomware.
- If you find a file that promises unrealistic things ( software to Medicines every program), guess what... Ransomware
- Dont open emails from people you don't know, especially when they promise you unrealistic things.
- Dont visit every stupid site you see on the net and furthermore don't download anything you see from it. It's your own greed that caused you the problem.
- I know it's been said 1000 times but for F@#$ Sake keep a backup of your most important files. Google gives 15GB, Mega gives 50Gb and there are many other solutions too. A movie or a program or even an mp3 can be found again, pictures of your loved ones, documents of your work, etc CAN NOT. Those don't even take a lot of space. Back them up ONLINE and off the PC.
- Always scan ANY INCOMING FILE. Have a folder named incoming or new or whatever, and always double, or even triple scan ANY file you download. Especially if it's from a source you don't know. It may be a slight inconvenience, but losing your valuable files and time, is more. Never assume anything is safe.
- Did I say to use common sense?
Sorry for the bad news but that's reality and I don't like to give people fake hopes. This thread will close soon, just leaving it on for possible questions, and I hope we all learned something.
FYI: For those who may not know, most of the time when we see a 4 letter word like ZZLA, WWKA, GUJD, UFWJ, MOQS, HHQA, PAAS, etc it probably means ransomware.
Last edited:
- Downloaded
- 233.6 GB
- Uploaded
- 31.2 TB
- Ratio
- 136.57
- Seedbonus
- 657,835
- Upload Count
- 12 (12)
Member for 9 years
@qime123 you need to use google because it is to long to type here how to remove this ransomware ...
this here is a little txt abouth wat is this ransomware ...
What is Moqs ransomware?
Moqs is a malicious program belonging to the Djvu ransomware family. It is designed to encrypt data and demand ransoms for the decryption. In other words, this ransomware renders files inaccessible, and victims are asked for payment - to recover access to their data.During the encryption process, affected files are appended with the ".moqs" extension. For example, a file initially named something like "1.jpg" would appear as "1.jpg.moqs", "2.jpg" as "2.jpg.moqs", "3.jpg" as "3.jpg.moqs", and so forth. After this process is complete, a ransom note is created in a text file titled "_readme.txt".
Moqs ransom note overview
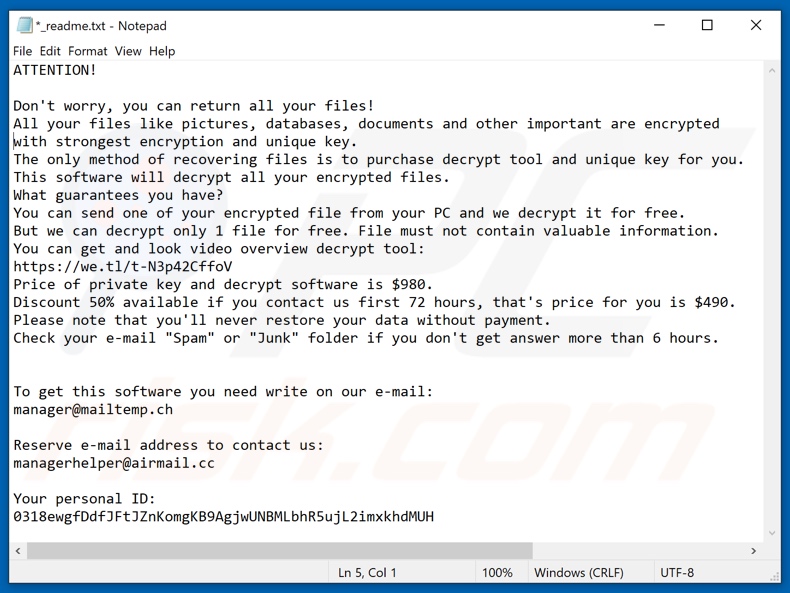
The ransom-demanding message ("_readme.txt") states that victims' databases, documents, pictures, and other important files have been encrypted. Decryption keys and tools must be purchased from the cyber criminals - to restore the data. The price of the recovery tools is stated to be 980USD.If victims establish contact with the criminals within 72 hours - the ransom will be reduced by 50% (490USD). Communication is to be held over email. Additionally, an encrypted file (which does not contain valuable information) can be attached to the emails; the decryption of this file will serve as proof that data restoration is possible.
Should no response from the cyber criminals arrive within 6 hours, victims are instructed to check their "Spam/Junk" email folders for the reply.
Moqs ransomware in detail
Unfortunately, in most ransomware infections, decryption is impossible without interference of the cyber criminals responsible. It might be if the malicious program is still in development and/or has significant flaws. Whatever the case, it is expressly advised against meeting the ransom demands.Despite paying, victims often do not receive the promised decryption tools. Therefore, their files remain encrypted (essentially worthless) and they experience a financial loss. To prevent Moqs ransomware from further encryptions, it must be removed from the operating system.
However, removal will not restore already compromised data. The only solution is recovering the files from a backup, if one was created before the infection and stored in a different location.
Screenshot of a message encouraging users to pay a ransom to decrypt their compromised data:
Similarities with other infections
Haron, Queclink, DECcenter, and Pause are a few examples of malicious programs within the ransomware category. This malware type operates by encrypting data and/or locking the device's screen - to demand payment for the decryption.
There are two significant differences in-between ransomware - the cryptographic algorithms it uses (symmetric or asymmetric) and the ransom size. To avoid permanent data loss, it is highly recommended to store backups in remote servers and/or unplugged storage devices (preferably, in multiple separate locations).
How did ransomware infect my computer?
Ransomware and other malware are commonly distributed via spam campaigns - large-scale operations during which thousands of deceptive/scam emails are sent. These letters can have infectious files attached to and/or linked inside them.
Malicious files can be in a variety of formats, e.g., PDF and Microsoft Office documents, archives (ZIP, RAR, etc.), executables (.exe, .run, etc.), JavaScript, and so on. When the files are executed, run, or otherwise opened - the infection chain is initiated.
Malicious programs (ransomware-types included) are typically disguised as or bundled with ordinary software/media. Untrustworthy download sources, e.g., unofficial and free file-hosting websites, Peer-to-Peer sharing networks, and other third-party downloaders - often offer malicious software.
Illegal activation ("cracking") tools and fraudulent updaters are prime examples of malware-spreading content. "Medicines" can infect systems instead of activating licensed products. Fake updaters cause infections by exploiting outdated program weaknesses and/or by installing malicious software rather than the updates.
Last edited:
- Downloaded
- 17.5 GB
- Uploaded
- 1.2 TB
- Ratio
- 72.33
- Seedbonus
- 627,743
- Upload Count
- 0 (0)
Member for 6 years
I hope you learned your lesson and that you'll avoid such things in the futureis form a friends laptop some kinds download free stuff
- Downloaded
- 233.6 GB
- Uploaded
- 31.2 TB
- Ratio
- 136.57
- Seedbonus
- 657,835
- Upload Count
- 12 (12)
Member for 9 years
- Status
- Not open for further replies.
